Node.js CTF, API Security, Protestware, Malicious Packages, Arbitrary File Writes and other news
wizer-ctf - An online website that features an interactive Capture The Flag challenge with vulnerable code examples that are taken from the JavaScript and Node.js domain. Great way to get into hacking and understanding the impact of insecure code.
Node API Security - Briefly exploring core concepts around Node API security with regards to GraphQL and REST API design with code examples specific to Node.js application servers.
Headlines
A deep-dive research paper on protestware - Remember node-ipc, left-pad, and faker security incidents? the research unveiled in this study categorizes the types of protestware campaigns, provides a comprehensive database and examines the impact on the ecosystem.
Malicious package repository - The OpenSSF maintains a repository on GitHub that can be used as a database of malicious packages (across ecosystems, JS included). It is to be used for malware reproduction, analysis, and study.
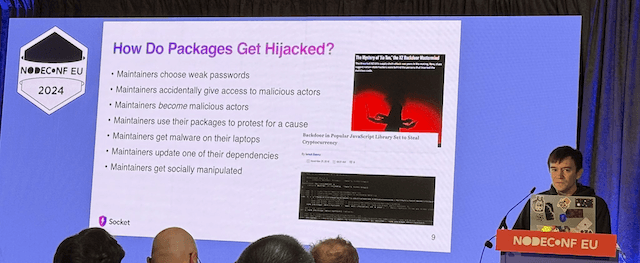
Mikola Lysenko at NodeConf EU shared insights about malicious packages and rogue campaigns on the npmjs registry:
Node.js delays semver-major PRs from immediate releases - To avoid breaking releases, changes introduced in semver-major pull requests will only land if they were added at least one month prior to the release date or received consensus from Node.js collaborators.
Deep research into arbitrary file write - Sonar security research shows how even security-hardened environments with low privileges and read-only file systems are susceptible to code execution due to internals of pipes usage in UNIX-based operating systems.
In-case you missed it… 10 Years Later - Congratulations Express 5.0 - Express 5.0 released officially with modern promise route handlers, application router, sane defaults for better DX and a security threat model, to name a few things 😅
📦 On npm
npm packages:
- ast-grep - ast-grep is a new tool for searching and managing your code at scale using a semantic search that is based on an abstract syntax tree.
- hey-how - Akash built an AI CLI that generates, explains, and executes commands inline. Think of it as a replacement for the Warp AI terminal program.
❗ New Security Vulnerabilities
- dom-iterator found vulnerable to CVE-2024-21541 Arbitrary Code Execution, 12 Nov 2024
- froala-editor found vulnerable to CVE-2024-51434 Cross-site Scripting, 7 Nov 2024
- cross-spawn found vulnerable to CVE-2024-21538 Regular Expression Denial of Service, 24 Oct 2024
🧠 Can you find the security vulnerability here?